- Make directory trees in a single swipe.
- Change the path; do not move the archive.
- Combine your commands with control operators.
- Quote variables with caution.
- Use escape sequences to manage long input.
- Group your commands together in a list.
- Use
xargsoutside offind. - Know when
grepshould do the counting -- and when it should step aside. - Match certain fields in output, not just lines.
- Stop piping
cats.
20061218
Adopting 10 good habits of Unix Scripting
I saw this on a quick fleeting moment on slash.dot .. It covers many things that I have done in the past..
20061120
Command Line Event Viewer
Every once in while microsoft does something correctly.. Found the command line event viewer.
Using command-line tools to manage events and event logs
You can also use command-line utilities to create and query event logs and associate programs with particular logged events. For example, you can use Eventcreate to customize an event entry to a specified event log. Eventquery.vbs is used to list the events and event properties from one or more event logs. Eventtriggers enables you to create event triggers that will run programs upon the occurrence of specific events.
20061119
Google Codesearch - Finding Vulns
Google Codesearch is a newer item in the google lab (Early October ). I like the functionality, but making all the code searchable will always find the bodies in the closet that not everyone wants to see.. The Google hacking database GHDB has been talking about it for awhile along with other noteable persons in the field.. just wondering if ISC/DSHIELD was interested in the topic for discussion..
The Search:
http://www.google.com/codesearch
Simple Buffer Overflows
Link: wikipedia Buffer_overflow
Search
lang:"c" strcpy buffer argv
or simply
buffer "should be big enough"
Using Google Code Search:
Found Examples of InSecure (Purposeful) Coding..Google Code Search
Finding Examples of correct implentation..Google Code Search
Possible Example of Real Vulnerability Finding... in Nachos Example Operating System
Link:Google Code Search
Site:Nachos URL
The Search:
http://www.google.com/codesearch
Simple Buffer Overflows
Link: wikipedia Buffer_overflow
Search
lang:"c" strcpy buffer argv
or simply
buffer "should be big enough"
Using Google Code Search:
Found Examples of InSecure (Purposeful) Coding..Google Code Search
/* vuln.c */
#include
int main(int argc, char * argv [])
{
char buffer [500];
if (argc > 1)
strcpy(buffer, argv[1]);
return (0);
}
#include
int main(int argc, char * argv [])
{
char buffer [500];
if (argc > 1)
strcpy(buffer, argv[1]);
return (0);
}
Finding Examples of correct implentation..Google Code Search
*hostdir = malloc(sizeof(char[strlen(argv[1])+1]));
/* separate hostname and dirname from 'hostname:dirname' format */
strcpy(hostdir, argv[1]);
/* separate hostname and dirname from 'hostname:dirname' format */
strcpy(hostdir, argv[1]);
Possible Example of Real Vulnerability Finding... in Nachos Example Operating System
#ifdef DEBUG
int main (int argc, char *
argv[]) {
char buffer[80];
printf ("string = %s.\n", strcpy (buffer, argv
[1]));
}
#endif
int main (int argc, char *
argv[]) {
char buffer[80];
printf ("string = %s.\n", strcpy (buffer, argv
[1]));
}
#endif
Link:Google Code Search
Site:Nachos URL
20061115
Combined Exploit Search Engine
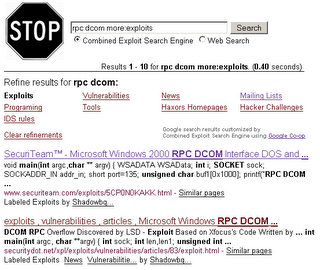
Combined Exploit Search Engine
Tweaked the Google Engine to include 150+ security websites from all over the globe.
Please join and collaborate.
Google Co-op release a couple weeks ago allows customization of the google engine..
20060904
XML to CSV transformation
Eh.. well since I was playing with new requirements.. (means new languages.. ruby)
I ended up coming up with a simple transformation of XML to CSV for data normalization.
I found this to be useful with "nmap -oX xmlout.xml" output switch
Anyway long story short here is the quick and dirty.
I ended up coming up with a simple transformation of XML to CSV for data normalization.
I found this to be useful with "nmap -oX xmlout.xml" output switch
Anyway long story short here is the quick and dirty.
# RUBY use of WIN32OLE
# Win32 OLE Q&A & Ruby stddoc
require 'win32ole'
excel = WIN32OLE.new('Excel.Application')
#excel['Visible'] = true
excel.workbooks.openxml({'Filename'=>'F:\xml_out.xml', 'LoadOption'=>2})
excel.ActiveWorkbook.SaveAs({'Filename'=>'F:\csv_in.csv','FileFormat'=>24, 'CreateBackup'=>'False'})
excel.quit
# Win32 OLE Q&A & Ruby stddoc
require 'win32ole'
excel = WIN32OLE.new('Excel.Application')
#excel['Visible'] = true
excel.workbooks.openxml({'Filename'=>'F:\xml_out.xml', 'LoadOption'=>2})
excel.ActiveWorkbook.SaveAs({'Filename'=>'F:\csv_in.csv','FileFormat'=>24, 'CreateBackup'=>'False'})
excel.quit
20060714
Python and Dabo
Since being pushed into Core (Impact), I've started to really dive in to some python coding.. To my total suprise there is a really great project in python called DABO! It is framework for GUI, database, and report generation. It would be nice to wrap a number of cli tools into a db based open source reporting tool. Wikto which is horrible at best for a gui, seems to be one of the wrap up tools in the win32 enviroment. I suppose that good wrapping (like the old cheops-ng) is inorder.. and to make it cross platform (thanks python wxpython) with professional output. Lets all start the integration engine... count down.
20060713
hdm - MOBB bug releases
[[hdm]] has been releasing a number browser bugs this month named MOBB(month of browser bugs). He was able to find these by running different browsers through DOM /CSS / and DHTML fuzzers in an attempt to crash the engines and other ways.
- Hamachi - DHTML fuzzer that recursively calls XMLHTTP in an attempt to iterate through arrays of possible DHTML element properties. It attempts format string vulnerabilities, long file paths, long urls, and difficult integer injection.
- CSS-Die - CSSDIE looks for common CSS1/CSS2/CSS3 implementation flaws by specifying common bad values for style values. This is similiar to Hamachi in that it performs format string vulnerabilities, long file paths, long urls, and difficult integer injection.
- DOM-Hanoi - DOM-Hanoi looks for common DHTML implementation flaws by adding/removing DOM elements. This is done through obj.appendChild and obj.removeChild methods.
- MangleMe - Mangleme sends format string vulnerabilities, bad characters, malformed javascript & applet requests, long urls, load requests with junk.
Most of his scripts have been attempting to locate vulnerabilities in the following browsers...
konqueror, safari, omniweb, opera, webTV, icab, ie6, mozilla
20060712
SANSFIRE 2006
WMI Promqry & Promqryui
-- wow windows actually has something of interest.
Spycar
-- IE browser malware checks
netstat (win32 xpsp2/2003)-- netstat -naob (shows dll linkage during mapping of executables/ports)
the -b switch adds some more interesting items.. but its slow... slow.
webgoat-- OWASP super buggy web-app for teaching secure coding.
Some how missed a few other tools this year such as wellenrieter, macshift, bidiblah, and nohup.
20060625
windump - finding the pcap device mapping
Looking at windump,( yeah.. for some reason I am currently sniffing in a windows enviroment) I was having a tough time locating the correct procedures for finding the capture device. I know that the devices can be located via the drop selection in Ethereal (WireShark June '06), but finding it from the command line provided to be difficult, especially via remote executions.
Why not use "windump -D", well.. I wanted to know the mappings of Local Area Connection. This script also allows for you parse its output encase you wanted to use it in conjunction with other remote execution methods such as wmic!
I have a quick vbs script that can read the registry and I've located a fairly easy lookup method.
Finding the Device from Regedit:
Example Comparision using search for "local"
Why not use "windump -D", well.. I wanted to know the mappings of Local Area Connection. This script also allows for you parse its output encase you wanted to use it in conjunction with other remote execution methods such as wmic!
I have a quick vbs script that can read the registry and I've located a fairly easy lookup method.
Finding the Device from Regedit:
- HKLM\SYSTEM\CurrentControlSet\Control\Network\
- Identify the Key set with the Value "{Default}" containing Data "Network Adapters "
- Search the listed Adapter for the Value Name containing the Data "Local Area Connection"
- The Key value that contains "Local Area Connection" is the reference to the physical device identifier
- Pre-append "\Device\NPF_" to the Key
- Example: \Device\NPF_{95007697-9E3B-41C0-9732-19063EBA4376}
- From this key: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet \Control\Network\{4D36E972-E325-11CE-BFC1-08002BE10318} \{95007697-9E3B-41C0-9732-19063EBA4376}
- This can be customized for running from any named connection identified from
- ipconfig /all
Example Comparision using search for "local"
C:\>cscript pcap_adapter.vbs "local" localhost -w test.txt
Microsoft (R) Windows Script Host Version 5.6
Copyright (C) Microsoft Corporation 1996-2001. All rights reserved.
Local Area Connection {EE878E44-6F4F-4CEB-93D3-3C9F8BB6B75C}
1 matches returned.
Finished writing to file. Results saved to test.txt
C:\>windump -D
1.\Device\NPF_GenericDialupAdapter (Generic dialup adapter)
2.\Device\NPF_{5A28A595-2DF1-4B68-84ED-9472E2B623C1} (Intel(R) PRO/Wireless 2915ABG Network Connection (Microsoft's Packet Scheduler) )
3.\Device\NPF_{EE878E44-6F4F-4CEB-93D3-3C9F8BB6B75C} (Broadcom NetXtreme Gigabit Ethernet Driver (Microsoft's Packet Scheduler) )
4.\Device\NPF_{768194C6-D64E-4C01-B933-1C1724B7DA9E} (VMware Virtual Ethernet Adapter)
5.\Device\NPF_{8941359A-87BF-4EDA-A287-A3A5B2AFF1B3} (VMware Virtual Ethernet Adapter)
Microsoft (R) Windows Script Host Version 5.6
Copyright (C) Microsoft Corporation 1996-2001. All rights reserved.
Local Area Connection {EE878E44-6F4F-4CEB-93D3-3C9F8BB6B75C}
1 matches returned.
Finished writing to file. Results saved to test.txt
C:\>windump -D
1.\Device\NPF_GenericDialupAdapter (Generic dialup adapter)
2.\Device\NPF_{5A28A595-2DF1-4B68-84ED-9472E2B623C1} (Intel(R) PRO/Wireless 2915ABG Network Connection (Microsoft's Packet Scheduler) )
3.\Device\NPF_{EE878E44-6F4F-4CEB-93D3-3C9F8BB6B75C} (Broadcom NetXtreme Gigabit Ethernet Driver (Microsoft's Packet Scheduler) )
4.\Device\NPF_{768194C6-D64E-4C01-B933-1C1724B7DA9E} (VMware Virtual Ethernet Adapter)
5.\Device\NPF_{8941359A-87BF-4EDA-A287-A3A5B2AFF1B3} (VMware Virtual Ethernet Adapter)
20060510
When {Puffy} Meets ^RedDevil^: Monkey tricks: Extracting Viruses/Worms
When {Puffy} Meets ^RedDevil^: Monkey tricks: Extracting Viruses/Worms
This is an extraordinary good point of reference for something I've been trying do with numerous tools. Though most of the time I end up rebuilding binary files from scratch using hexworkshop and ethereal / packetyzer... This is great!
This is an extraordinary good point of reference for something I've been trying do with numerous tools. Though most of the time I end up rebuilding binary files from scratch using hexworkshop and ethereal / packetyzer... This is great!
20060427
More work..
Built fpg(a false positive generator) from FLop to test an IDS the other day. Pretty nice. I know there are others called stik.. & something else. Might even send the picture post card to the addy in the INSTALL.
Busy as a bee building interfaces for sguil and the IDS fleet. Wrote a bunch of VBS scripts as well that can interface fairly nicely with wmic and AD.. hey at least the MCSE comes in handy in that respect. blah. Hopefully I will find a place once the server is up to post this garbage.
Busy as a bee building interfaces for sguil and the IDS fleet. Wrote a bunch of VBS scripts as well that can interface fairly nicely with wmic and AD.. hey at least the MCSE comes in handy in that respect. blah. Hopefully I will find a place once the server is up to post this garbage.
20060426
Tail -f Unix through JAVA
I've been wandering around the internet looking for a good way to implement the tail -f unix within java. If your unfamiliar with tail, well.. shame.
Tail -f Unix
This tutorial is actually really nice.. If you look around you will notice
Tail-f Unix across a client-server relationship
Tail -f Unix
This tutorial is actually really nice.. If you look around you will notice
Tail-f Unix across a client-server relationship
20060418
Mind Movement
Visual Basic Scripting, mainly Active Directory, has been taking a large portion of my life recently. I've been nose deep in vbs / cscritpting cli's and bring forth my powers of tcl.tk to bear as well. Who knows maybe somebody will eventually like my code.. blah!
I dont understand why microsoft doesnt more easily disimenate information about included files and stuctures.. thats really annoying to me.
"~:\Program Files\Microsoft Office\OFFICE11\1033\VBSCRIP5.CHM"
Thats an fairly good start especially if your looking at :
"mk:@MSITStore:~:\Program%20Files\Microsoft%20Office\OFFICE11\1033 /\VBSCRIP5.CHM::/html/vsgrpFeatures.htm"
I ended up with some great code from http://www.kouti.com/scripts.htm
With that as a base.. I've made some really great cli/pipeable tools to replace all the crap of dsget.exe.
I dont understand why microsoft doesnt more easily disimenate information about included files and stuctures.. thats really annoying to me.
"~:\Program Files\Microsoft Office\OFFICE11\1033\VBSCRIP5.CHM"
Thats an fairly good start especially if your looking at :
"mk:@MSITStore:~:\Program%20Files\Microsoft%20Office\OFFICE11\1033 /\VBSCRIP5.CHM::/html/vsgrpFeatures.htm"
I ended up with some great code from http://www.kouti.com/scripts.htm
With that as a base.. I've made some really great cli/pipeable tools to replace all the crap of dsget.exe.
Other Active Directory and Services are pestering my mind as well..
- Numerous general tools such as ADfind and SVCutil are big help
Additional kung-fu from WMIC interfaces
Subscribe to:
Comments (Atom)


