Using command-line tools to manage events and event logs
You can also use command-line utilities to create and query event logs and associate programs with particular logged events. For example, you can use Eventcreate to customize an event entry to a specified event log. Eventquery.vbs is used to list the events and event properties from one or more event logs. Eventtriggers enables you to create event triggers that will run programs upon the occurrence of specific events.
20061120
Command Line Event Viewer
Every once in while microsoft does something correctly.. Found the command line event viewer.
20061119
Google Codesearch - Finding Vulns
Google Codesearch is a newer item in the google lab (Early October ). I like the functionality, but making all the code searchable will always find the bodies in the closet that not everyone wants to see.. The Google hacking database GHDB has been talking about it for awhile along with other noteable persons in the field.. just wondering if ISC/DSHIELD was interested in the topic for discussion..
The Search:
http://www.google.com/codesearch
Simple Buffer Overflows
Link: wikipedia Buffer_overflow
Search
lang:"c" strcpy buffer argv
or simply
buffer "should be big enough"
Using Google Code Search:
Found Examples of InSecure (Purposeful) Coding..Google Code Search
Finding Examples of correct implentation..Google Code Search
Possible Example of Real Vulnerability Finding... in Nachos Example Operating System
Link:Google Code Search
Site:Nachos URL
The Search:
http://www.google.com/codesearch
Simple Buffer Overflows
Link: wikipedia Buffer_overflow
Search
lang:"c" strcpy buffer argv
or simply
buffer "should be big enough"
Using Google Code Search:
Found Examples of InSecure (Purposeful) Coding..Google Code Search
/* vuln.c */
#include
int main(int argc, char * argv [])
{
char buffer [500];
if (argc > 1)
strcpy(buffer, argv[1]);
return (0);
}
#include
int main(int argc, char * argv [])
{
char buffer [500];
if (argc > 1)
strcpy(buffer, argv[1]);
return (0);
}
Finding Examples of correct implentation..Google Code Search
*hostdir = malloc(sizeof(char[strlen(argv[1])+1]));
/* separate hostname and dirname from 'hostname:dirname' format */
strcpy(hostdir, argv[1]);
/* separate hostname and dirname from 'hostname:dirname' format */
strcpy(hostdir, argv[1]);
Possible Example of Real Vulnerability Finding... in Nachos Example Operating System
#ifdef DEBUG
int main (int argc, char *
argv[]) {
char buffer[80];
printf ("string = %s.\n", strcpy (buffer, argv
[1]));
}
#endif
int main (int argc, char *
argv[]) {
char buffer[80];
printf ("string = %s.\n", strcpy (buffer, argv
[1]));
}
#endif
Link:Google Code Search
Site:Nachos URL
20061115
Combined Exploit Search Engine
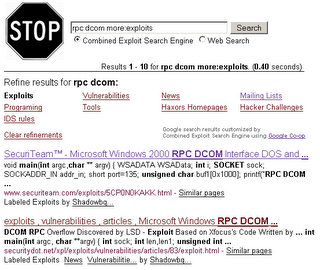
Combined Exploit Search Engine
Tweaked the Google Engine to include 150+ security websites from all over the globe.
Please join and collaborate.
Google Co-op release a couple weeks ago allows customization of the google engine..
Subscribe to:
Posts (Atom)









